Problem Statement
-
Overly Complex
Admins must navigate complicated interfaces and spend hours manually assigning permissions across layers of users and roles. Error-Prone
Manual handling increases risk of misconfigured permissions, exposing sensitive data or creating productivity roadblocks.Inflexible
Static role structures don't match real-world team dynamics. It's hard to support edge cases like contractors, matrix teams, or cross-functional project access.Opaque to Users
End-users don’t know why they don’t have access to certain features. Admins must explain and troubleshoot constantly.
UX Solution: Smart Permission Management System
A modular, intuitive permission management UX built to simplify complexity, reduce security risk, and scale with the organization. We introduce a Role-Based + Contextual Access System with intelligent visualizations and delegated management.
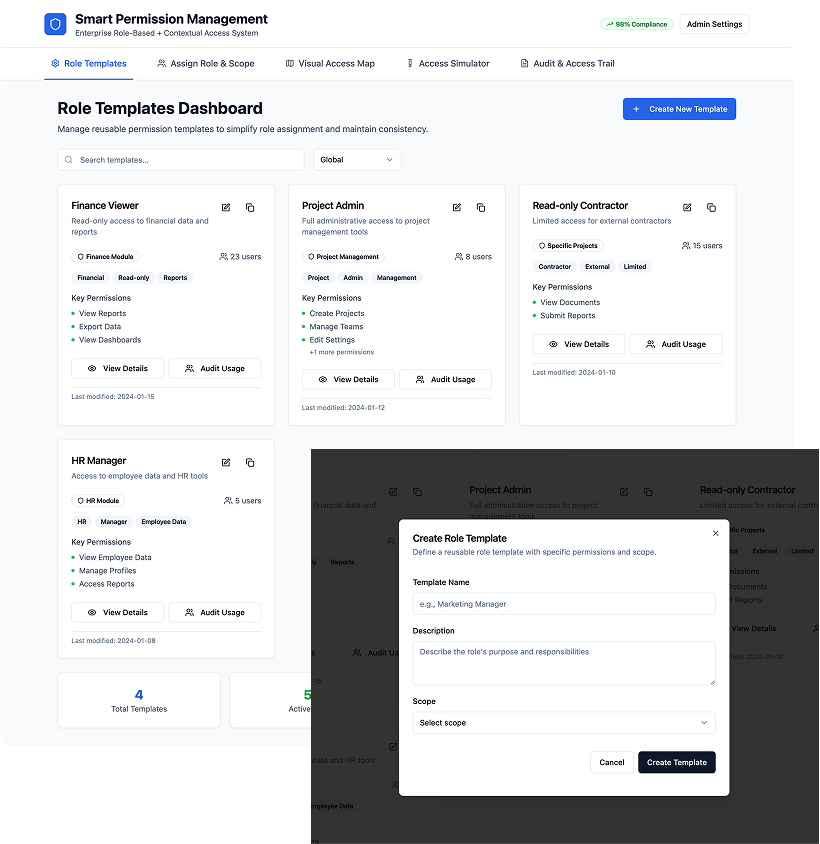
1. Role Templates Dashboard
Purpose:
• Give IT/Admins a central place to manage reusable permission templates.
Components:
• List of pre-defined role templates (e.g., Finance Viewer, Project Admin, Read-only Contractor)
• "Create New Template" flow
• Tags showing scope (Module/Project/Team access)
• Audit button to see who’s using it
Solves:
• Reduces manual work by offering reusable role presets. Makes role creation scalable.
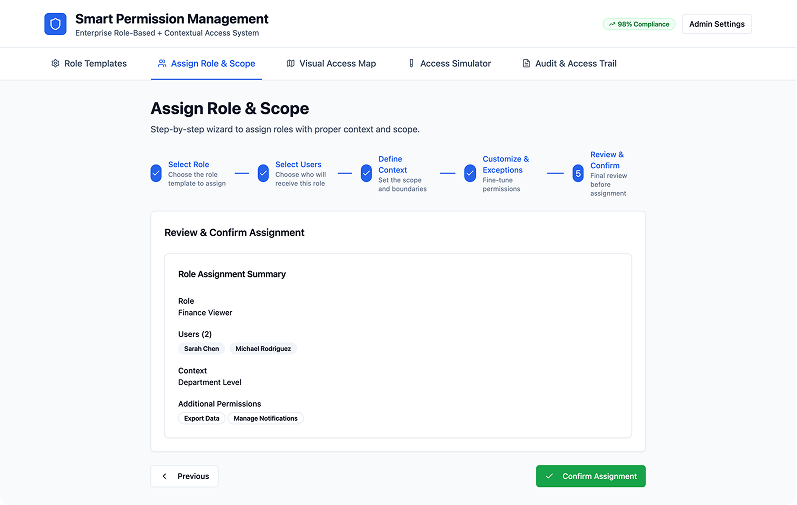
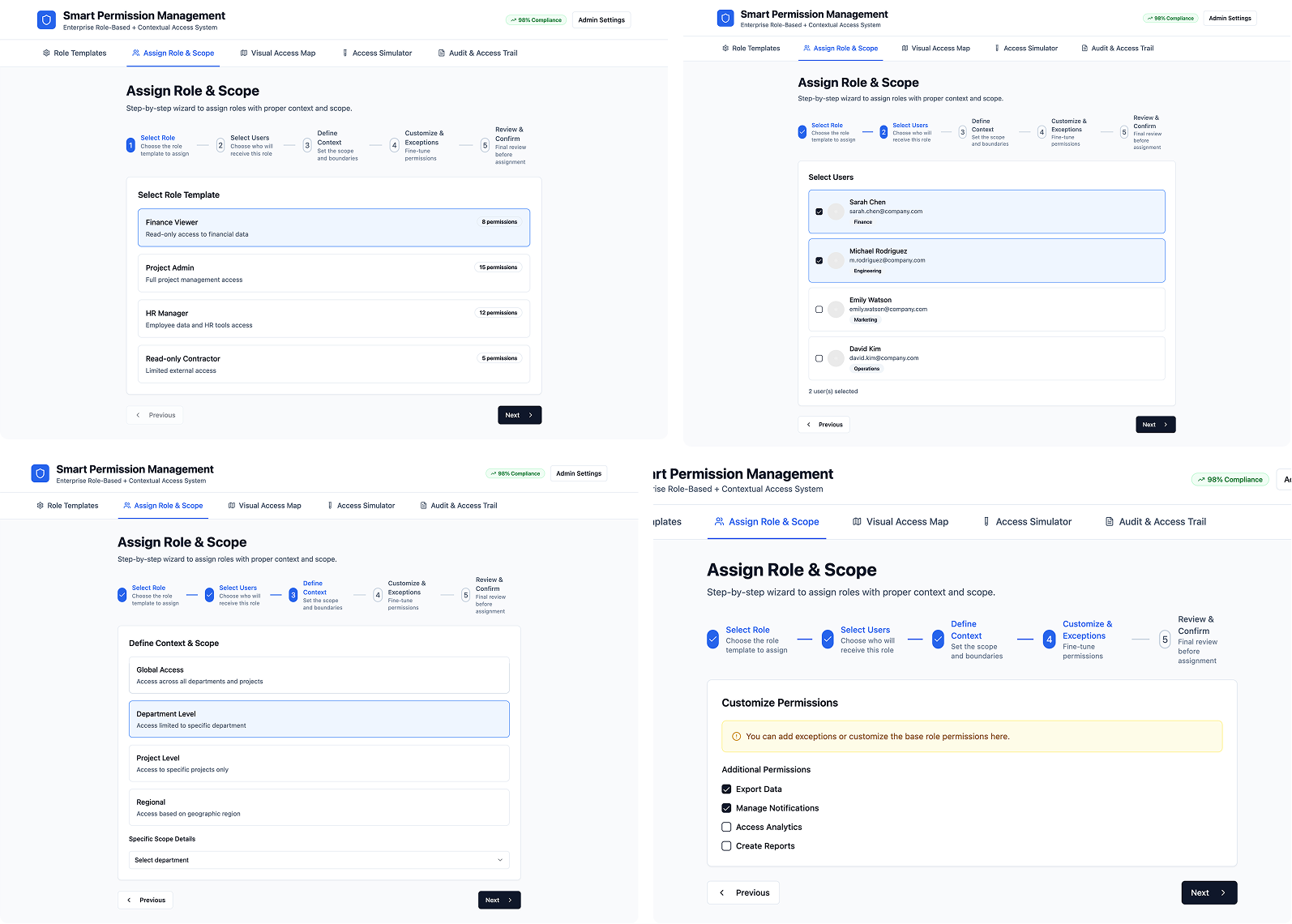
2. Assign Role & Scope Wizard
Purpose:
• Assign users to roles in an intelligent step-by-step interface.
Components:
• Step 1: Select Role
• Step 2: Select Context (Project, Department, Region)
• Step 3: Customize scope or exceptions
• Final Review + Confirm
Solves:
• Prevents misassignment and lets roles adapt to organizational needs. Reduces IT dependency by enabling scoped delegation.
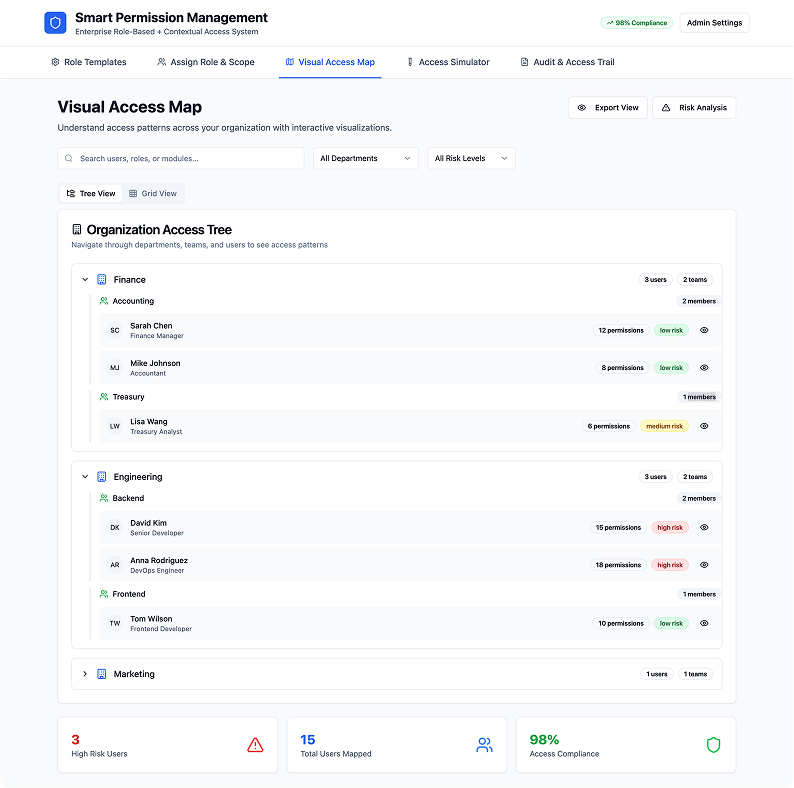
3. Visual Access Map (Tree + Grid UI)
Purpose:
• Help Admins or Managers understand access visually across orgs and projects.
Components:
• Tree diagram by Org > Team > Role > User
• Grid view for “who has access to what”
• Hover/click to reveal access reason or source
• Search + filters (by user, module, date, etc.)
Solves:
• Removes opaqueness. Empowers audit and quick troubleshooting. Gives clarity to non-technical stakeholders too.
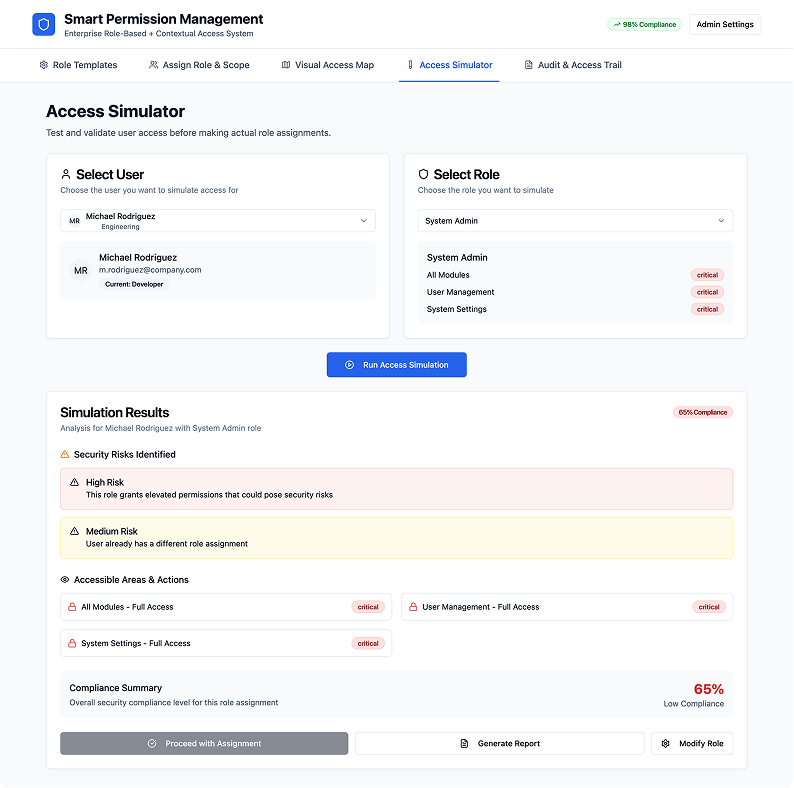
4. Access Simulator
Purpose:
• Simulate a user's access before assigning it.
Components:
• Input: select user and potential role
• Output: list of accessible actions, data, and areas
• “Red flags” for overlapping roles or elevated permissions
Solves:
• Reduces costly mistakes and security gaps. Makes permissions testable, not guessable.
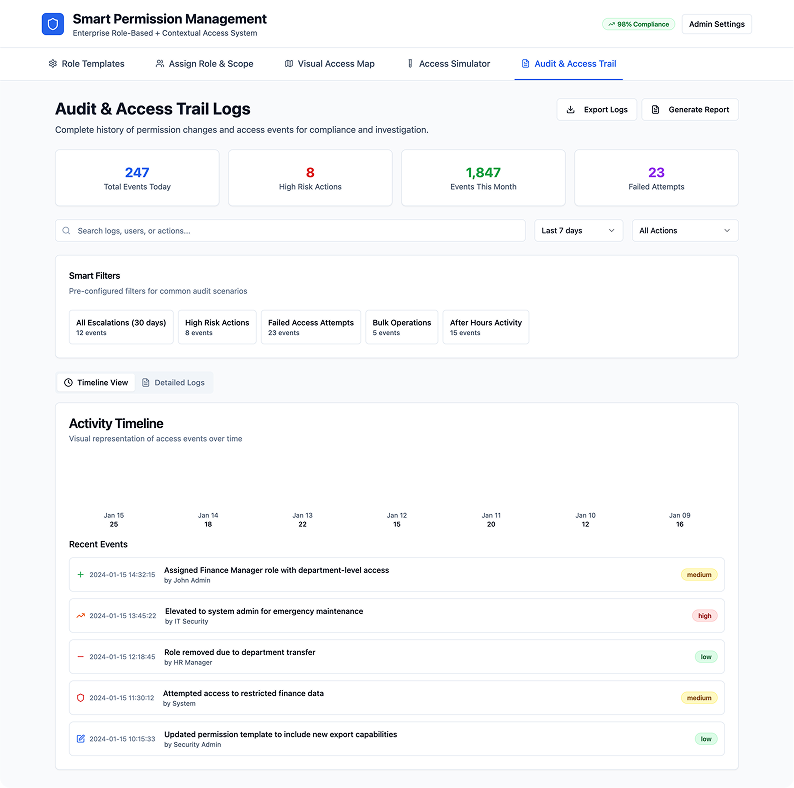
5. Audit & Access Trail Logs
Purpose:
• Give security teams and auditors clear history of permission changes.
Components:
• Timeline of access changes (who added/removed what, when)
• Exportable logs
• “Smart Filters” (e.g., "Show all access escalations in the past 30 days")
Solves:
• Supports compliance, accountability, and faster incident investigation.